Strengthening Security Across Your GKE Clusters Using Cloud Native Security Tools

Overview
Kubernetes has quickly become the backbone of modern application delivery and Google Kubernetes Engine (GKE) simplifies much of the operational overhead. But as clusters grow and workloads multiply, even small misconfigurations can create serious security blind spots. Over the last few years, I’ve seen organizations struggle not because they lack tools but because they lack visibility and consistent guardrails.
This blog highlights the practical steps and security practices that actually strengthen GKE clusters, not just theoretically but in day-to-day operations.
Why GKE Security Matters
Kubernetes is powerful, but its flexibility can introduce security risks if not properly managed. Misconfigurations, exposed APIs, and lack of access controls are just a few of the vulnerabilities that can compromise a GKE cluster. Given that Kubernetes orchestrates critical business processes and handles sensitive data, securing your GKE environment is crucial for maintaining business continuity and protecting customer trust.
This is where vulnerability management tools become essential. By proactively identifying and addressing security weaknesses, these tools are essential for maintaining the integrity and security of your GKE clusters.
Understanding GKE Security Posture
Your GKE security posture refers to the overall security health of your Kubernetes environment, encompassing everything from the configuration of individual nodes to the management of secrets and network policies. A strong security posture means,
- misconfigurations are detected early,
- least-privilege access is enforced, and
- the cluster can withstand both external threats and accidental internal risks.
How Vulnerability Tools Enhance GKE Security
Vulnerability scanners help automate the otherwise time-consuming job of identifying weak points across container images, workloads, and cluster configurations. In GKE, these scanners can flag outdated packages, vulnerable images, privilege escalations, and policy violations. Key capabilities include
- Automated Scanning: Regular scans of your GKE clusters to detect vulnerabilities in real-time.
- Compliance Checks: Ensuring that your Kubernetes environment adheres to industry best practices and regulatory standards.
- Misconfiguration Detection: Identifying and alerting on any misconfigurations that could expose your clusters to security risks.
- Patch Management: Helping you stay on top of updates and patches, ensuring that all components of your GKE clusters are up-to-date and secure.
- Detailed Reporting: Providing insights into the security status of your clusters, with actionable recommendations for remediation.
Choosing the Right Vulnerability Tool for GKE
Different teams have different needs. Before selecting a tool, evaluate how well it integrates with your CI/CD pipelines, whether it supports cluster-wide scanning, and how it handles multi-cloud or hybrid environments. Simplicity and clarity in reporting are just as important as feature breadth. Here are some considerations when evaluating vulnerability management tools:
- Integration: The tool should seamlessly integrate with GKE and your existing CI/CD pipelines.
- Scalability: It should be capable of handling the scale of your operations, regardless of the size of your Kubernetes deployments.
- Ease of Use: A user-friendly interface and clear documentation are essential for effective management.
- Real-time Monitoring: The ability to provide real-time insights and alerts is crucial for staying ahead of potential threats.
- Support for Multi-Cloud: If your organization operates in a multi-cloud environment, the tool should support multiple cloud providers, not just Google Cloud.
Best Practices for GKE Security
While scanners are essential, they must work alongside core security practices, such as:
- Least Privilege Access: Implementing IAM policies that adhere to the principle of least privilege, ensuring that users and service accounts have only the permissions they need.
- Network Segmentation: Using Kubernetes network policies to control traffic between pods, reducing the attack surface.
- Regular Audits: Conducting periodic security audits of your GKE clusters to identify and remediate potential vulnerabilities.
- Continuous Monitoring: Setting up continuous monitoring to detect suspicious activity or changes in your clusters.
Business Benefits of Using a GKE Vulnerability Tool
Organizations implementing systematic vulnerability scanning typically see:
- Enhanced Security: Proactively identifies and mitigates vulnerabilities, reducing the risk of data breaches and cyberattacks.
- Compliance Assurance: Ensures adherence to industry standards and regulatory requirements, minimizing legal and financial liabilities.
- Operational Efficiency: Automates security checks and patch management, saving time and reducing manual effort.
- Cost Savings: Prevents costly security incidents by addressing issues before they escalate, optimizing resource usage.
- Improved Trust: Builds customer confidence by demonstrating a strong commitment to securing sensitive data and applications.
- Scalability: Adapts to growing infrastructure needs, ensuring security measures keep pace with business expansion.
- Real-time Protection: Offers immediate insights and alerts, enabling swift response to emerging threats.
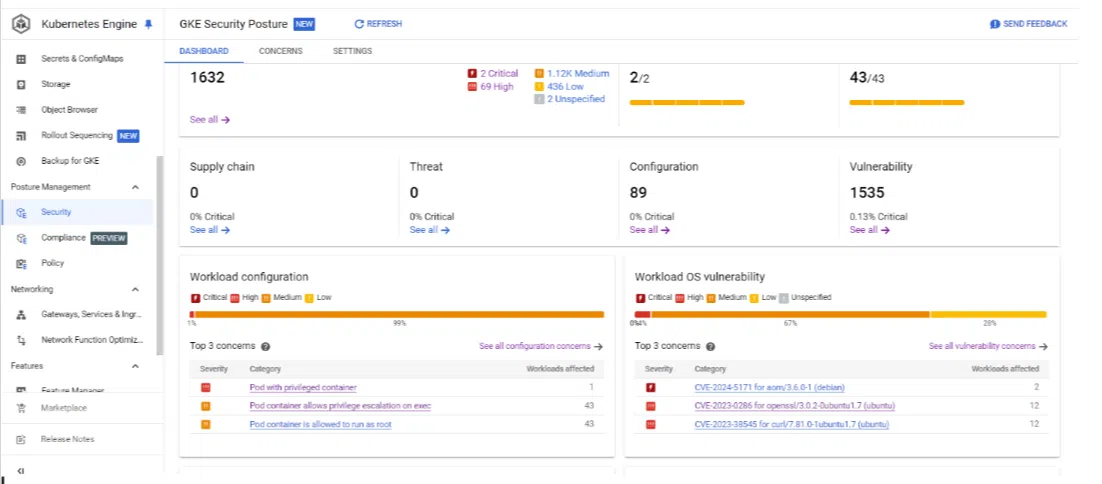
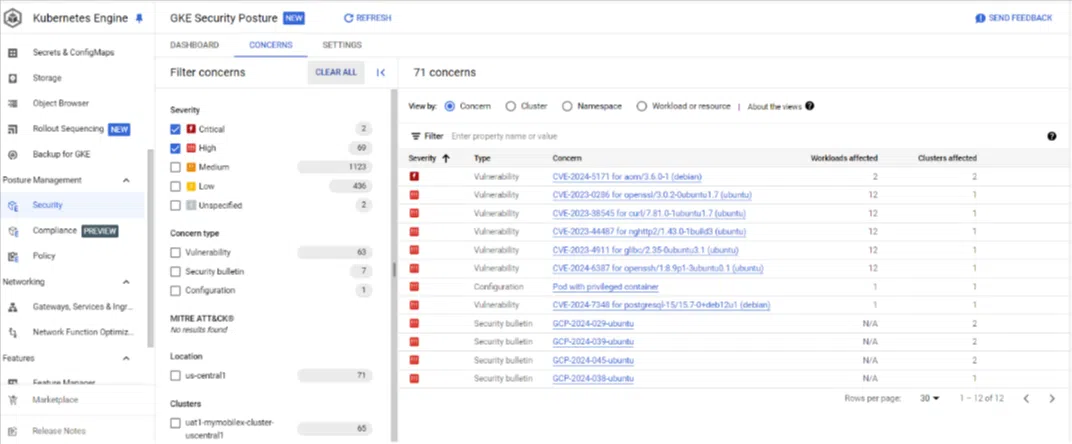
Screenshot of the risks which detects by vulnerability scanner of Kubernetes cluster
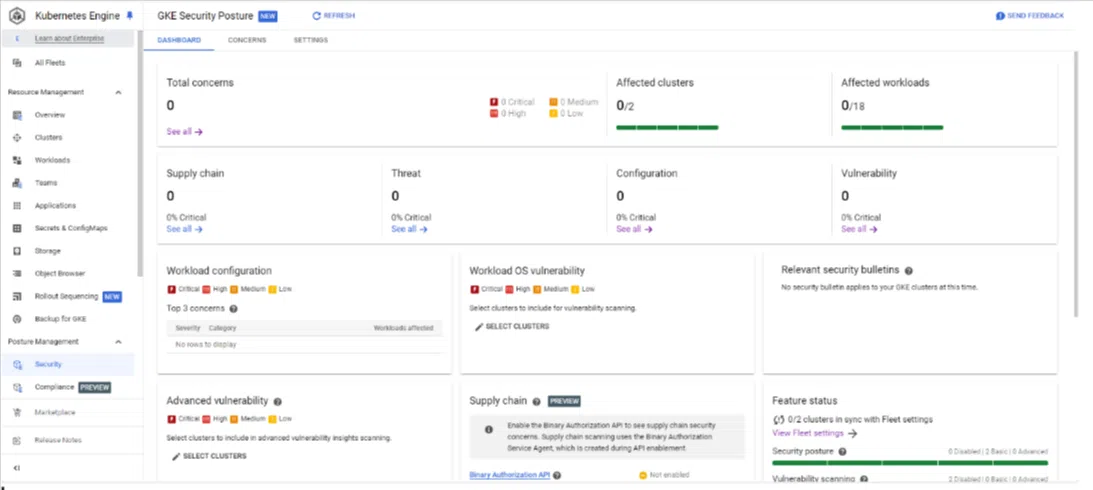
Screenshot of the vulnerability scanner when all risks got resolved
Conclusion
In the evolving landscape of cloud-native security, maintaining a strong GKE security posture is more important than ever. Vulnerability management tools are a vital part of this strategy, providing the insights and automation needed to protect your Kubernetes environment from emerging threats. By integrating these tools into your security workflows and adhering to best practices, you can ensure that your GKE clusters remain secure, resilient, and compliant.

Keyur is a Cloud & DevOps Lead Architect with 16+ years of experience across AWS, Azure, and GCP. He specializes in automation, Kubernetes, and cloud migrations, helping teams build secure, scalable, and cost-efficient systems. His passion lies in simplifying complex architectures and enabling faster, reliable delivery.